Sha Algorithm Sha algorithm cryptography hash secure methods sha1 hashing dsa modern problem flaws solutions outside cryptographic techgenix standard giorgio cis readings
If you are looking for What Is SHA-256 Algorithm: How it Works and Applications [2022 Edition you've came to the right web. We have 35 Pictures about What Is SHA-256 Algorithm: How it Works and Applications [2022 Edition like Secure Hash Algorithm (SHA-1) | Download Scientific Diagram, Google Announces Plans to Discontinue Support of SHA-1 Certificates and also What is SHA-256 Algorithm and how Does It Function in the Bitcoin Network?. Here it is:
What Is SHA-256 Algorithm: How It Works And Applications [2022 Edition
sha algorithm simplilearn buffers
SHA-1 Computation SHA-224 & SHA-256 Computation The Message Digest Is
 www.researchgate.net
www.researchgate.net
computation hash sha256 variables
SHA-1 - What Is Secure Hash Algorithm-l (SHA-1)? - Computer Notes
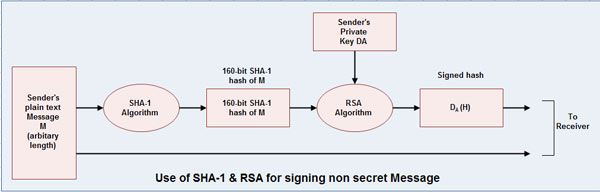 ecomputernotes.com
ecomputernotes.com
sha hash secure algorithm security computer ll ecomputernotes
Cryptography Methods: Flaws, Solutions, And Outside Threads
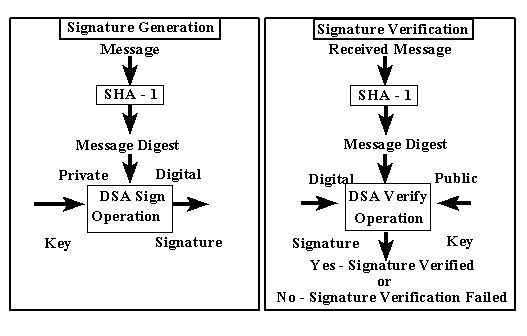 techgenix.com
techgenix.com
sha algorithm cryptography hash secure methods sha1 hashing dsa modern problem flaws solutions outside cryptographic techgenix standard giorgio cis readings
Structure Of SHA-3 Algorithms
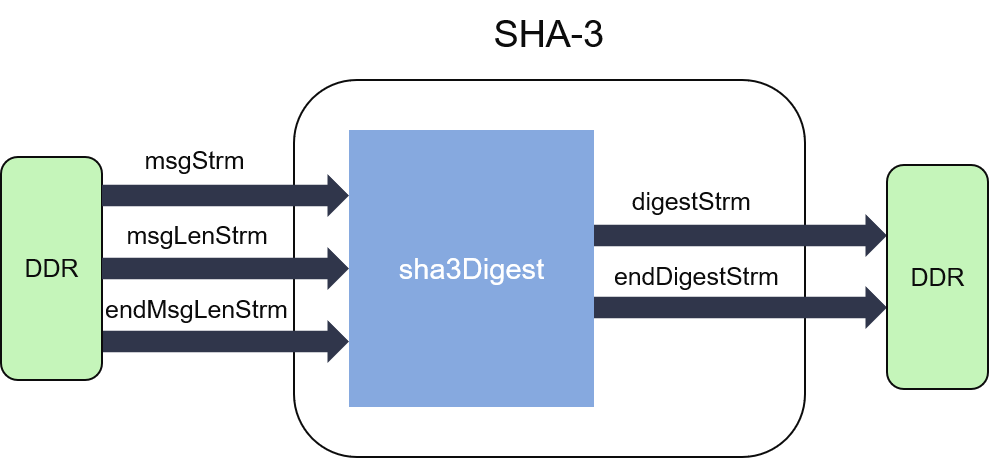 xilinx.github.io
xilinx.github.io
SHA-1 - YouTube
 www.youtube.com
www.youtube.com
sha
Hashing Algorithms | All Cloud Miners
 www.allcloudminers.com
www.allcloudminers.com
mining algorithm sha 256 bitcoin cloud diagram algorithms hashing security optimize
SHA Algorithm | Characteristics | Uses And Types Of SHA Algorithm
 www.educba.com
www.educba.com
sha educba
SHA- Secure Hashing Algorithm
 www.slideshare.net
www.slideshare.net
hashing
Block Diagram Of The SHA-256 Algorithm | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net
sha
12 Remarkable Difference Between MD5 And SHA-1 With Table - Core
 coredifferences.com
coredifferences.com
md5 sha difference between remarkable table
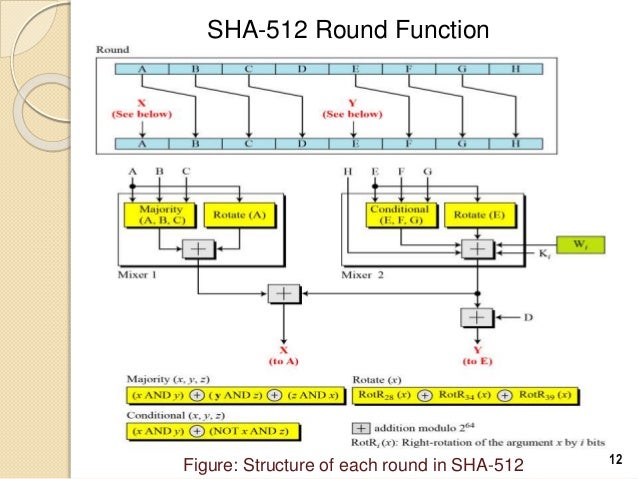
Structure Of SHA-512 Algorithm | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net
algorithm hgoa pseudo methodology
What Is SHA-256 Algorithm: How It Works And Applications [2022 Edition
sha simplilearn
How SHA (Secure Hash Algorithm) Works? | By Marcello Faria | Medium
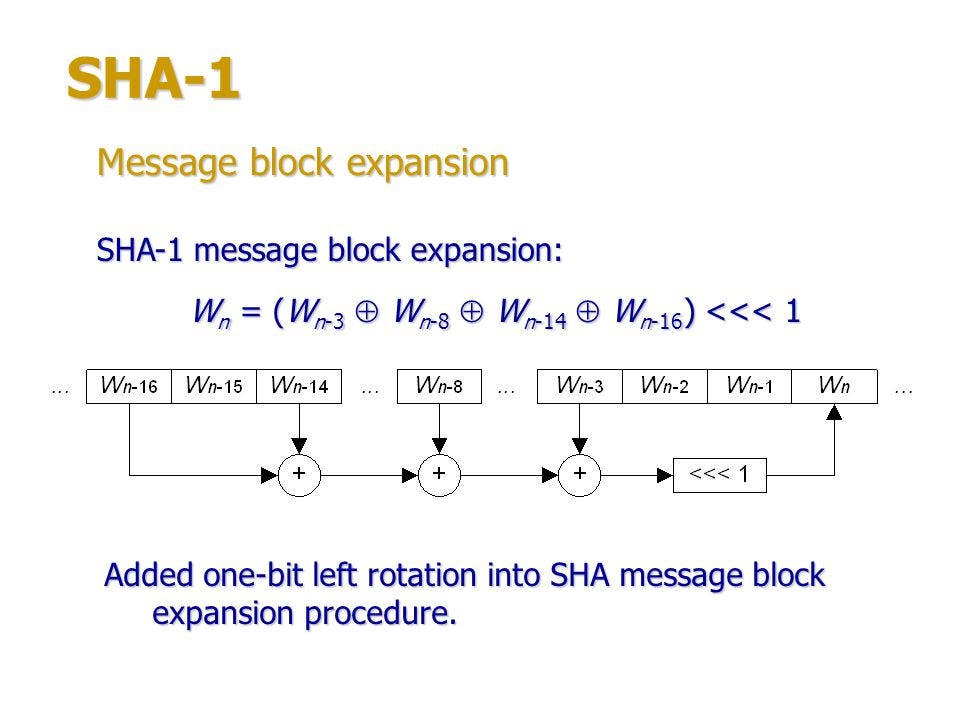 01faria-marcello.medium.com
01faria-marcello.medium.com
hash
C Implementation Of SHA-256 Algorithm | Semantic Scholar
 www.semanticscholar.org
www.semanticscholar.org
algorithm sha
What Is SHA-256 Algorithm: How It Works And Applications [2022 Edition
applications simplilearn
Hash - Algorithm Complexity & Security: MD5 Or SHA1? - Stack Overflow
 stackoverflow.com
stackoverflow.com
md5 sha1 vs algorithm hash sha256 secure better security bits which sha between than cryptography comparison complexity generates because questions
SHA 256 Algorithm - YouTube
 www.youtube.com
www.youtube.com
algorithm
SHA Algorithm | Characteristics | Uses And Types Of SHA Algorithm
 www.educba.com
www.educba.com
educba
Algorithm Design - Why Does SHA-1 Rotate The Variables A And B
 crypto.stackexchange.com
crypto.stackexchange.com
sha algorithm why rotate does variable variables specific reason there
PPT - PROJECT : ALGORITHM SHA-1 PowerPoint Presentation, Free Download
 www.slideserve.com
www.slideserve.com
algorithm sha project definition ppt powerpoint presentation produces hash
What Is SHA Or Secure Hash Algorithm?
 thecustomizewindows.com
thecustomizewindows.com
hash algorithm secure sha thecustomizewindows refers
SHA-1 Secure Hash Function IP Core
 www.alma-technologies.com
www.alma-technologies.com
sha1 algorithm alma
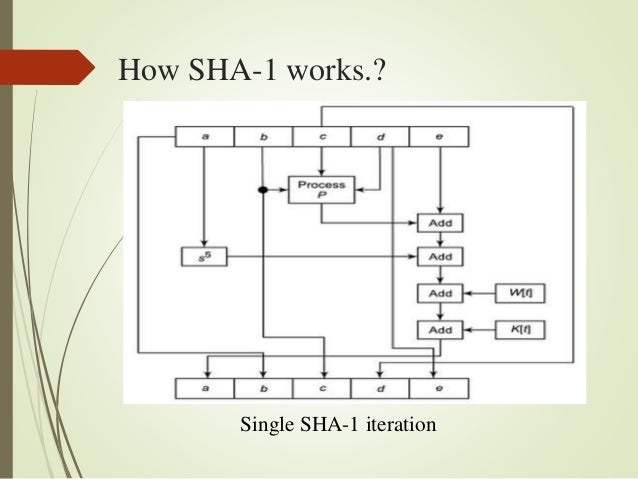
Secure Hash Algorithm (SHA-512)
 www.slideshare.net
www.slideshare.net
sha512
SHA-2 Encryption Algorithm: Does It Really Improves Website Security?
 cheapsslsecurity.com
cheapsslsecurity.com
sha algorithm encryption improves security website
What Is SHA-256 Algorithm: How It Works And Applications [2022 Edition
sha simplilearn
Secure Hash Algorithm - YouTube
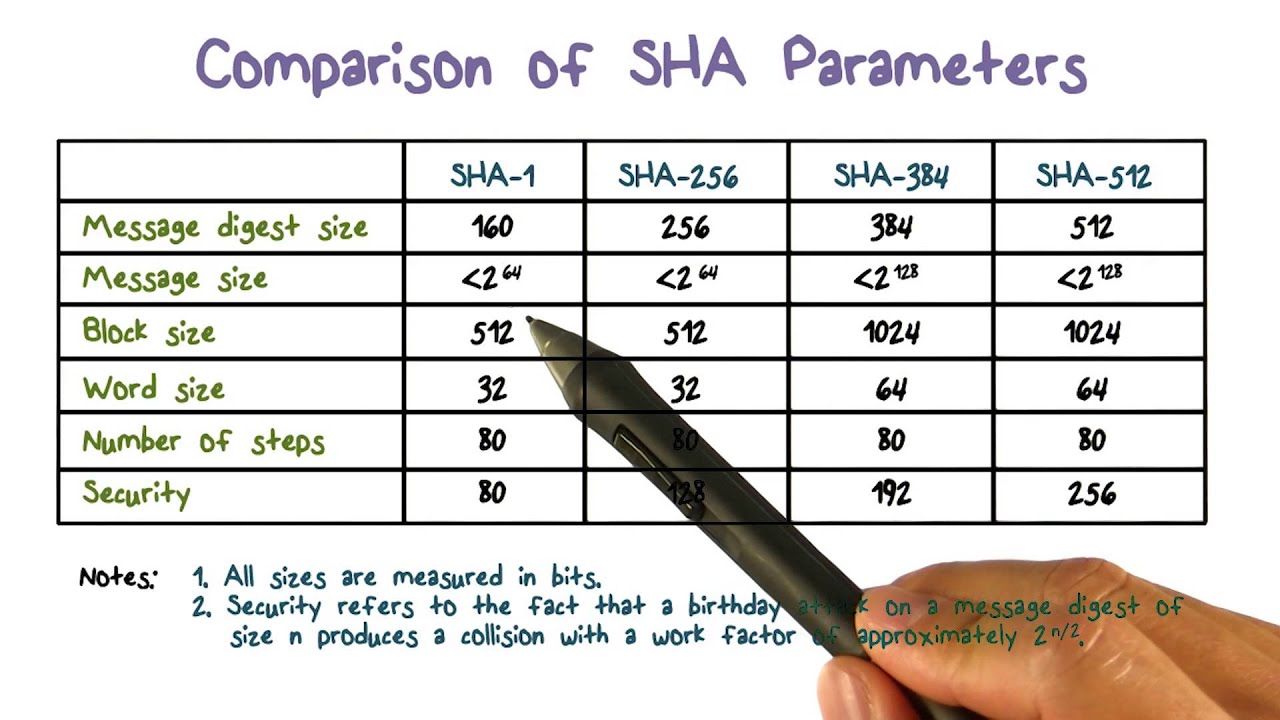 www.youtube.com
www.youtube.com
hash algorithm secure
PPT - SHA (secure Hash Algorithm) PowerPoint Presentation - ID:6450319
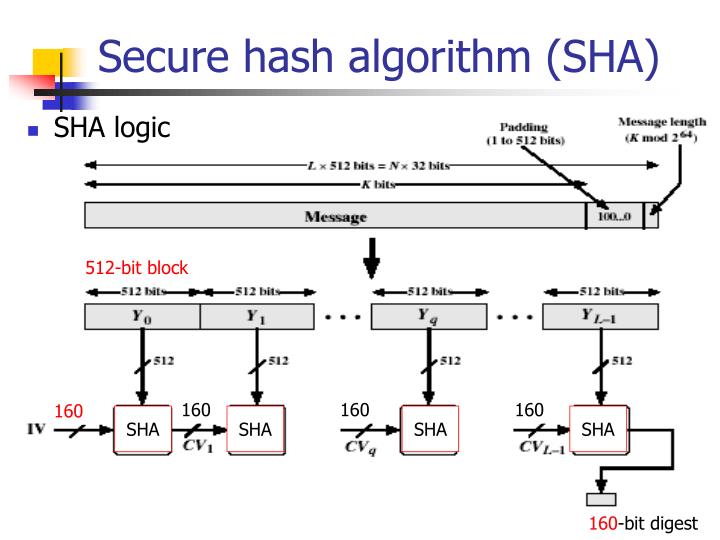 www.slideserve.com
www.slideserve.com
hash algorithm sha secure logic ppt powerpoint presentation
Secure Hash Algorithm (SHA-1) | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net
The Difference Between SHA-1, SHA-2 And SHA-256 Hash Algorithms
 www.ssl2buy.com
www.ssl2buy.com
hashing algorithms ssl2buy security thoughtsmag techbriefly
SHA-1 Algorithm Steps | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net
What Is SHA-256 Algorithm And How Does It Function In The Bitcoin Network?
 waytomine.com
waytomine.com
sha 256 algorithm bitcoin function does blockchain network mining
Google Announces Plans To Discontinue Support Of SHA-1 Certificates
 www.tripwire.com
www.tripwire.com
sha sha1 md5 hashing hash function security wikipedia rounds algorithm algorithms between sha2 sha512 difference compression state tripwire iteration within
CryptoURANUS Economics: SHA-256 Hash-Algorithm: Cryptocurrency
 www.cryptouranus.com
www.cryptouranus.com
sha algorithm
Secure Hash Algorithm
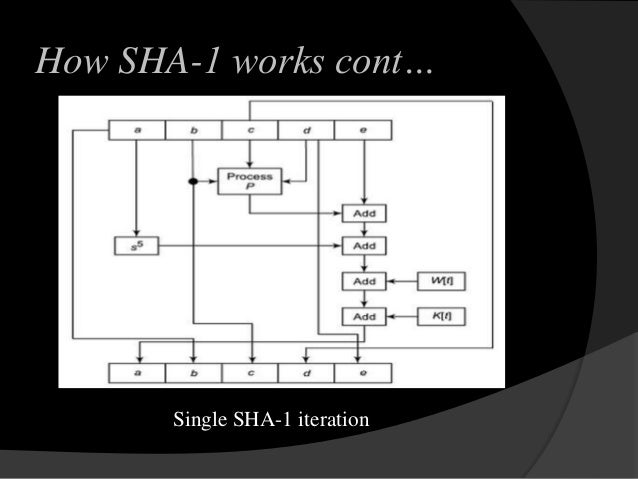 es.slideshare.net
es.slideshare.net
Secure hash algorithm. Algorithm sha project definition ppt powerpoint presentation produces hash. Sha algorithm encryption improves security website
